To secure the communication between your Site and Citrix Workspace app for Mac, you can integrate your connections with a range of security technologies, including Citrix Gateway. For information about configuring Citrix Gateway with Citrix StoreFront, see StoreFront documentation.
Note:
Citrix recommends using Citrix Gateway to secure communications between StoreFront servers and users’ devices.
Note:
Starting with macOS Catalina, Apple has enforced extra requirements for root CA certificates and intermediate certificates which administrators must configure. For more information, see Apple Support article HT210176.
To enable remote users to connect to your XenMobile deployment through Citrix Gateway, you can configure Citrix Gateway to support StoreFront. The method for enabling access depends on the edition of XenMobile in your deployment.
If you deploy XenMobile in your network, allow connections from internal or remote users to StoreFront through Citrix Gateway, by integrating Citrix Gateway with StoreFront. This deployment allows users to connect to StoreFront to access published applications from XenApp and virtual desktops from XenDesktop. Users connect through Citrix Workspace app for Mac.
If the Citrix Secure Web Gateway Proxy is installed on a server in the secure network, you can use the Citrix Secure Web Gateway Proxy in Relay mode. For more information about Relay mode, see XenApp and Citrix Secure Web Gateway documentation.
If you’re using Relay mode, the Citrix Secure Web Gateway server functions as a proxy and you must configure Citrix Workspace app for Mac to use:
The FQDN must list, in sequence, the following three components:
For example, my_computer.example.com is an FQDN, because it lists, in sequence, a host name (my_computer), an intermediate domain (example), and a top-level domain ( com ). The combination of intermediate and top-level domain ( example.com ) is referred to as the domain name.
Proxy servers are used to limit access to and from your network, and to handle connections between Citrix Workspace app for Mac and servers. Citrix Workspace app for Mac supports both SOCKS and secure proxy protocols.
When the Citrix Workspace app for Mac communicates with the Web server, it uses the proxy server settings configured for the default web browser on the user device. Configure the proxy server settings for the default Web browser on the user device accordingly.
Starting with the version 2405, you can use multiple proxy servers that allow the HDX sessions to select appropriate proxy servers for accessing specific resources. This selection is based on the proxy rules configured in the Proxy Auto‑Configuration (PAC) file. Using this file, you can manage the network by mentioning which network traffic must be sent through a proxy server and which must be sent directly. Additionally, the PAC URL supports both http:// and file:// protocols.
Network firewalls can allow or block packets based on the destination address and port. Citrix Workspace app for Mac must be able to communicate through the firewall with both the Web server and Citrix server. The firewall must permit HTTP traffic (often over the standard HTTP port 80 or 443 for a secure Web server) for user device to Web server communication. For Citrix Workspace to Citrix server communication, the firewall must permit inbound ICA traffic on ports 1494 and 2598.
Transport Layer Security (TLS) is the latest, standardized version of the TLS protocol. The Internet Engineering Taskforce (IETF) renamed it TLS when it took over responsibility for the development of TLS as an open standard.
TLS secures data communications by providing server authentication, encryption of the data stream, and message integrity checks. Some organizations, including U.S. government organizations, require the use of TLS to secure data communications. These organizations might also require the use of validated cryptography, such as Federal Information Processing Standard (FIPS) 140. FIPS 140 is a standard for cryptography.
Citrix Workspace app for Mac supports RSA keys of 1024, 2048, and 3072-bit lengths. Root certificates with RSA keys of 4096-bit length are also supported.
Note:
Citrix Workspace app for Mac uses platform (OS X) crypto for connections between Citrix Workspace app for Mac and StoreFront.
The following cipher suites are deprecated for enhanced security:
Citrix Workspace app for Mac supports only the following cipher suites:
For DTLS 1.0 users, Citrix Workspace app for Mac 1910 and later supports only the following cipher suite:
Upgrade your Citrix Gateway version to 12.1 or later if you want to use DTLS 1.0. Otherwise, it falls back to TLS based on the DDC policy.
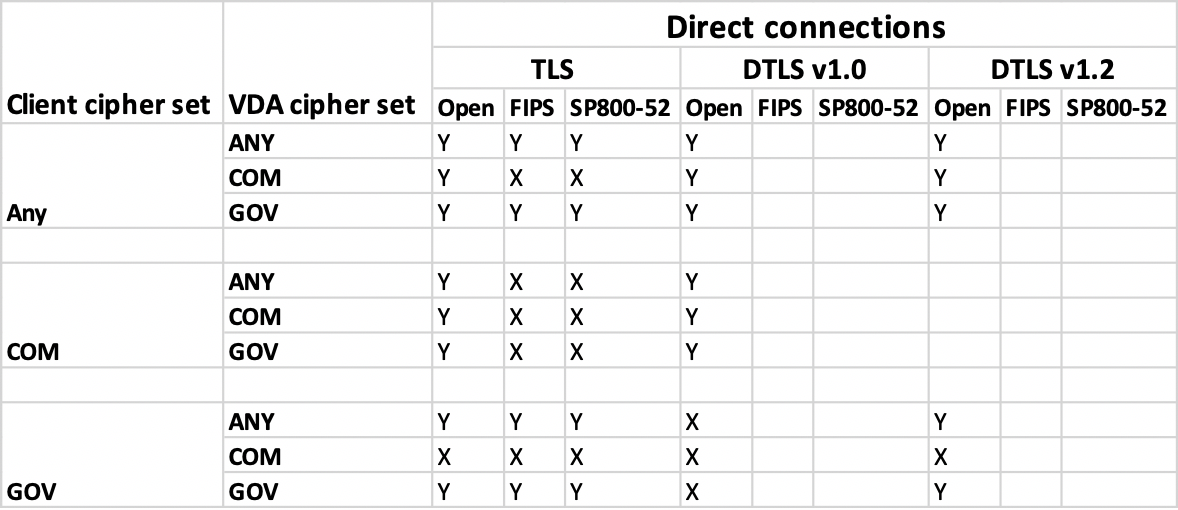
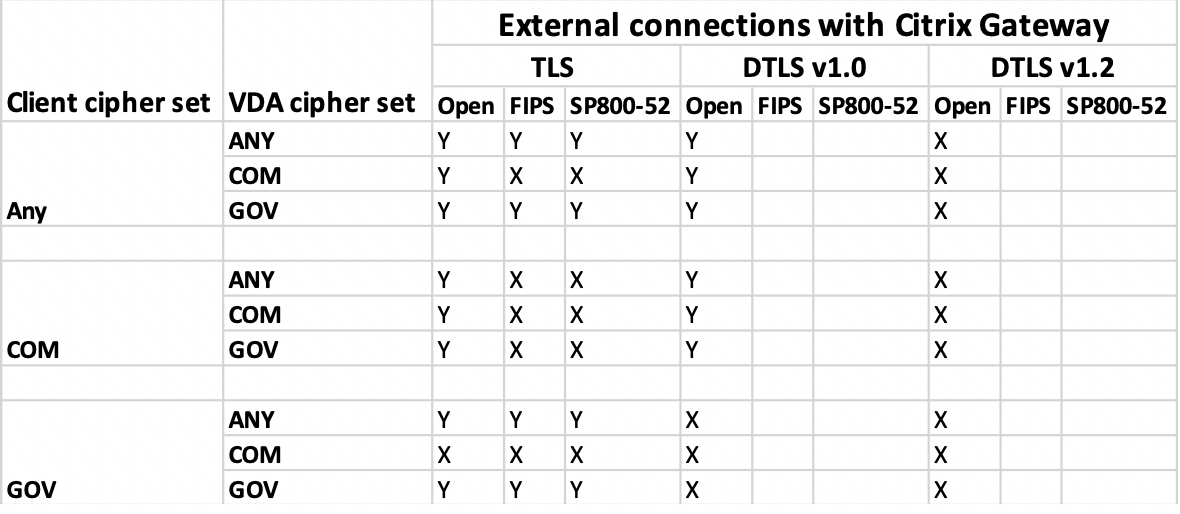
The following matrices provide details of internal and external network connections:

There are two main steps involved in setting up TLS:
To use TLS to secure communications between TLS-enabled Citrix Workspace app for Mac and the server farm, you need a root certificate on the user device. This root certificate verifies the signature of the Certificate Authority on the server certificate.
macOS X comes with about 100 commercial root certificates already installed. However, if you want to use another certificate, you can obtain one from the Certificate Authority and install it on each user device.
Install the root certificate on each device, depending on your organization’s policies and procedures, instead of prompting users to install it. The easiest and safest way is to add root certificates to the macOS X keychain.
The root certificate is installed and used by TLS-enabled clients and by any other application using TLS.
This section provides information for configuring security policies for ICA sessions over TLS. You can configure certain TLS settings used for ICA connections in Citrix Workspace app for Mac. These settings are not exposed in the user interface. Changing them requires running a command on the device running Citrix Workspace app for Mac.
Note:
TLS policies are managed in other ways - by devices controlled by an OS X server or another mobile device management solution.
TLS policies include the following settings:
SecurityComplianceMode. Sets the security compliance mode for the policy. If you don’t configure SecurityComplianceMode, FIPS is used as the default value. Applicable values for this setting include:
defaults write com.citrix.receiver.nomas SecurityComplianceMode SP800-52
SecurityAllowedTLSVersions. Specifies the TLS protocol versions that are accepted during protocol negotiation. This information is represented as an array and any combination of the possible values is supported. When this setting isn’t configured, the values TLS10, TLS11, and TLS12 are used as the default values. Applicable values for this setting include:
defaults write com.citrix.receiver.nomas SecurityAllowedTLSVersions -array TLS11 TLS12
SSLCertificateRevocationCheckPolicy. Improves the cryptographic authentication of the Citrix server and improves the overall security of the SSL/TLS connections between a client and a server. This setting governs the handling of a trusted root certificate authority (CA) while opening a remote session through SSL when using the client for OS X.
When you enable this setting, the client checks whether the server’s certificate is revoked. There are several levels of certificate revocation list checking. For example, the client can be configured to check only its local certificate list, or to check the local and network certificate lists. In addition, certificate checking can be configured to allow users to log on only if all Certificate Revocation lists are verified.
Certificate Revocation List (CRL) checking is an advanced feature supported by some certificate issuers. It allows admins to revoke security certificates (invalidated before their expiry date) if there is cryptographic compromise of certificate private keys, or unexpected changes in the DNS name.
Applicable values for this setting include:
Note:
If you don’t set SSLCertificateRevocationCheckPolicy, FullAccessCheck is used as the default value. defaults write com.citrix.receiver.nomas SSLCertificateRevocationCheckPolicy FullAccessCheckAndCRLRequired
To configure TLS settings on an unmanaged computer, run the defaults command in Terminal.app.
defaults is a command line application that you can use to add, edit, and delete app settings in an OS X preferences list file.
To change settings:
defaults write com.citrix.receiver.nomas
: The name of the setting as described earlier.
: A switch identifying the type of the setting, either -string or -array. If the setting type is a string, this setting can be omitted.
: The value for the setting. If the value is an array and multiple values need to be specified, separate the values with a space.
defaults write com.citrix.receiver.nomas SecurityAllowedTLSVersions -array TLS11 TLS12
To reset a setting back to its default:
defaults delete com.citrix.receiver.nomas
: The name of the setting as described earlier.
defaults delete com.citrix.receiver.nomas SecurityAllowedTLSVersions
Security improvements and enhancements were introduced with Citrix Receiver for Mac version 12.3, including the following:
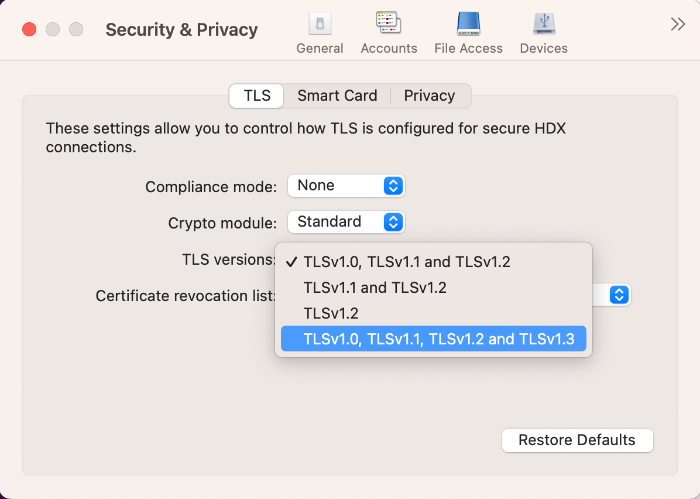
The improved Security and Privacy screen includes the following new options in the TLS tab:
The following image illustrates the Security and Privacy settings accessible from the UI:
The official version of this content is in English. Some of the Cloud Software Group documentation content is machine translated for your convenience only. Cloud Software Group has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Cloud Software Group product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Cloud Software Group, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Cloud Software Group will not be held responsible for any damage or issues that may arise from using machine-translated content.
DIESER DIENST KANN ÜBERSETZUNGEN ENTHALTEN, DIE VON GOOGLE BEREITGESTELLT WERDEN. GOOGLE LEHNT JEDE AUSDRÜCKLICHE ODER STILLSCHWEIGENDE GEWÄHRLEISTUNG IN BEZUG AUF DIE ÜBERSETZUNGEN AB, EINSCHLIESSLICH JEGLICHER GEWÄHRLEISTUNG DER GENAUIGKEIT, ZUVERLÄSSIGKEIT UND JEGLICHER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, DER EIGNUNG FÜR EINEN BESTIMMTEN ZWECK UND DER NICHTVERLETZUNG VON RECHTEN DRITTER.
CE SERVICE PEUT CONTENIR DES TRADUCTIONS FOURNIES PAR GOOGLE. GOOGLE EXCLUT TOUTE GARANTIE RELATIVE AUX TRADUCTIONS, EXPRESSE OU IMPLICITE, Y COMPRIS TOUTE GARANTIE D'EXACTITUDE, DE FIABILITÉ ET TOUTE GARANTIE IMPLICITE DE QUALITÉ MARCHANDE, D'ADÉQUATION À UN USAGE PARTICULIER ET D'ABSENCE DE CONTREFAÇON.
ESTE SERVICIO PUEDE CONTENER TRADUCCIONES CON TECNOLOGÍA DE GOOGLE. GOOGLE RENUNCIA A TODAS LAS GARANTÍAS RELACIONADAS CON LAS TRADUCCIONES, TANTO IMPLÍCITAS COMO EXPLÍCITAS, INCLUIDAS LAS GARANTÍAS DE EXACTITUD, FIABILIDAD Y OTRAS GARANTÍAS IMPLÍCITAS DE COMERCIABILIDAD, IDONEIDAD PARA UN FIN EN PARTICULAR Y AUSENCIA DE INFRACCIÓN DE DERECHOS.
本服务可能包含由 Google 提供技术支持的翻译。Google 对这些翻译内容不做任何明示或暗示的保证,包括对准确性、可靠性的任何保证以及对适销性、特定用途的适用性和非侵权性的任何暗示保证。このサービスには、Google が提供する翻訳が含まれている可能性があります。Google は翻訳について、明示的か黙示的かを問わず、精度と信頼性に関するあらゆる保証、および商品性、特定目的への適合性、第三者の権利を侵害しないことに関するあらゆる黙示的保証を含め、一切保証しません。
ESTE SERVIÇO PODE CONTER TRADUÇÕES FORNECIDAS PELO GOOGLE. O GOOGLE SE EXIME DE TODAS AS GARANTIAS RELACIONADAS COM AS TRADUÇÕES, EXPRESSAS OU IMPLÍCITAS, INCLUINDO QUALQUER GARANTIA DE PRECISÃO, CONFIABILIDADE E QUALQUER GARANTIA IMPLÍCITA DE COMERCIALIZAÇÃO, ADEQUAÇÃO A UM PROPÓSITO ESPECÍFICO E NÃO INFRAÇÃO.